This is what happens when you visit slashgeek.net. It informs three other websites of your presence. This is not something I consciously and intentionally did to track you down and record all your steps and every little click you make. This is the result of having a mid-level, somewhat functional, website. Yes I could remove all the analytic/social media codes and it would stop tracking you but it wouldn’t make the site much functional for majority of the users.
But this is nothing compared to the amount of tracking and sharing of information some of the big sites do. Try it yourself with Collusion for firefox. As you visit more site you will soon find yourself stuck in a web of trackers which knows your every step and click, and by the end of the day probably knows more about your habit and patterns than you do.
But some people don’t mind being tracked. They would rather have advertisers give them relevant ads and search engines give them relevant results and websites give them relevant content. But this post is not about them, this post is about the minority of those who take their privacy seriously.
Privacy is not cheap.
I don’t mean this only in the monetary sense. Total anonymity comes with a cost. The cost of speed, functionality, relevancy, eye-candy, etc. You can’t have all. You have to make a choice that is not open to compromise.
When you visit a website, the site can have your location based on the IP address of your ISP (Internet Service Provider). The ISP has logs of your internet connections and browsing data which they sell to the highest bidder. The websites you visit usually have (at the minimum) analytic that logs your browsing pattern; which includes the search term you used to visit the site, the browser you are using, your IP, your operating system, your location, your time, the outgoing links you are clicking, the duration you spent on the site when was your last visit. Among other things. The social media widget tracks the contents you are reading and the people you are sharing it with (among other things). The dynamic ads know the search term or the incoming link you used to visit the site and the contents you are reading and then give you ads based on this information.
Some people might have a problem with this.
There is a level of anonymity you can have. Are you trying to be anonymous because you don’t like being tracked or you pose a threat to a subversive government or maybe you are a secret super spy trying to stay under? For each case, there is a need for a different level of precaution. We are going to look into some of the best anonymity practices out there.
DOs & DON’T for paranoia level anonymity
DON’T
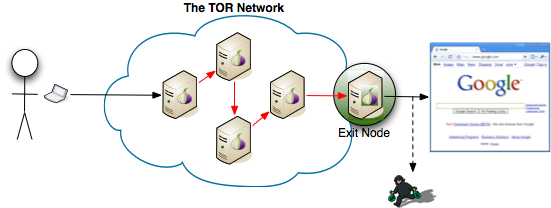
use Tor, exclusively. Tor is usually the go-to service for people looking for easy peasy anonymity. Tor gives you anonymity (to a certain extent) but doesn’t always protect your privacy. To make it harder/safer to identify you, go for: You -> VPN -> Tor. At the end of the day, your exit Tor node can still see your data so it might be a good idea not to use tor when going through a password protected sites you care about. Yes, it most likely will make your browsing excruciatingly slow and have a google (or other services) throw you captchas for every once in a while. To avoid google annoying you, try You -> Tor -> VPN but this is much harder to configure.
DO
set up your own VPN server. Don’t go for third party VPN providers even if they claim to purge logs. Get a VPS server not located in your country. Cheap, high, and fast bandwidth VPS are a dime a dozen. Don’t stick with one VPS, for long. Change every month, nuke/reset your VPS before you leave. You should also look into a mode of payment for your VPS that doesn’t reveal your personal information.
DON’T
use Google. It’s hard to replace Google as a good search engine. Google is in the business of following your every step. They spend a lot of money and do in-depth research to find better ways to track you and they are very good at it. Instead use DuckDuckGo, their privacy reputation is pretty solid. Their search results are not so bad either. You could also try Ixquick as a second option.
DO
use Firefox. For me, it’s not a choice based on fanboyism, I much rather like Chrome if privacy is not an issue. The choice of Firefox is for two reasons: The organization behind the browser is non-profit and the main reason being the privacy extension choice for firefox is much better (and have more control) than chrome. The three must install Firefox extension for privacy are:
Ghostery: Ghostery sees the “invisible” web, detecting trackers, web bugs, pixels, and beacons placed on web pages by Facebook, Google Analytics, and over 800 other ad networks, behavioral data providers, web publishers – all companies interested in your activity.
NoScript: Allow active content to run only from sites you trust, and protect yourself against XSS and Clickjacking attacks.
Adblock Plus: The add-on is supported by over forty filter subscriptions in dozens of languages which automatically configure it for purposes ranging from removing online advertising to blocking all known malware domains.
This is pretty much the safest anonymous setup you can get. It might be slow, hard, and time-consuming to set up but if you are worried about your privacy and anonymity then you shouldn’t mind doing the extra work.