If you are horrified to find out how easy it is to reset a Windows password you are in for a treat. To reset Linux root password you don’t even need a live distro. Going with “if you have physical access to a computer all bets are off“ philosophy. Resetting the Linux root password is as easy as they come.
There is more than one way to skin this cat, but I will show you one of the easiest option and how it’s done with Ubuntu. Though I haven’t tried it on every garden variety Linux distros out there, to the best of my knowledge this works on all major Linux distro out there.
Prerequisite:
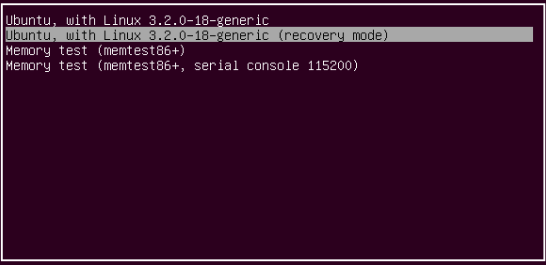
Being able to boot into recovery mode. With Ubuntu, you get prompt to log in to recovery mode or different kernel version, whenever you boot up.
Step 1:
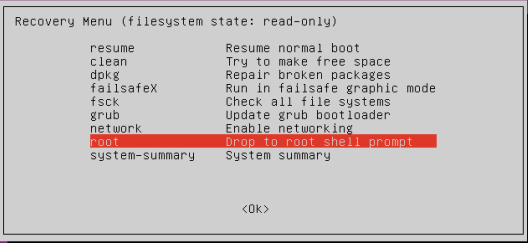
Once you boot in to the recovery mode you will get a prompt with recovery options. Chose root Drop to root shell prompt. 2 minutes in and you already have root access to the box. Scary huh?
Step 2:
Once you have root access with recovery mode you will need write access in order to reset/change root password. Type this:
mount -o remount,rw / this will mount your root diectory with read/write permission.
Step 3:
Type passwd and you will get prompted to type in new root password and verify it by retyping the password. If you want to reset a specific user’s password just add the username passwd username.
Sure you can take steps to prevent someone from resetting your password so easily. But once someone has physical access to your Linux box with the default install option, this is as easy as it gets.